Another Reason NOT to Use Microsoft for Your DNS Server
I used to have one (1) out of my four DNS servers that was a Microsoft NT box… but that was a LONG time ago! Now it is all Linux! Anyway, if you do have a Microsoft Windows DNS server… well… you are in for it!
Microsoft DNS Server Attacks Continue
“In an advisory this morning borrowing language used during previous statements about completely different exploits, Microsoft’s Security Response Center team confirmed that it has seen at least one new wave of attacks based on proof-of-concept code impacting its DNS server software in Windows Server-based systems. The concept enables malicious users to run code remotely under the system privileges generally granted to the DNS service itself. Although technically, the exploit does not directly threaten Internet routing the same way as the crafted IPv6 header problem in Cisco routers that also periodically rears its ugly head (or heads its ugly rear), this exploit can impact the routing of e-mail and other IP traffic within an enterprise or limited domain. Yesterday, Microsoft acknowledged that the proof-of-concept code discovered by engineers and reported by BetaNews was responsible for the first rash of attacks. But that acknowledgment was confused by multiple press sources as having been an indication that the code was just released, when in fact, the code may have been publicly disseminated for at least a matter of weeks, if not longer.”
Microsoft also says they are in no big hurry to fix it… so don’t hold your breath!
Don’t Hold Your Breath for a MS DNS Hole Patch
Microsoft says it hopes to patch the hole in its Domain Name System Server—which is now leaving vulnerable PCs open to a worm attack—by “no later” than Patch Tuesday in May. Microsoft teams are working around the world and around the clock to get a fix out for the May 8 security bulletin release, the MSRC’s Christopher Budd wrote in the security center’s blog on Tuesday night. Budd said that Microsoft teams are now developing and testing 133 separate updates, including one in every language for every currently supported version of Windows servers. ‘Each of these has to be tested to ensure they effectively protect against the vulnerability,’ Budd said. ‘Because DNS is a critical part of the networking infrastructure, they also have to be tested to ensure that changes introduced by the updates don’t pose a greater risk than the security issue we’re addressing.'”
 Say it ain’t so! Well, maybe… we’ll see!
Say it ain’t so! Well, maybe… we’ll see!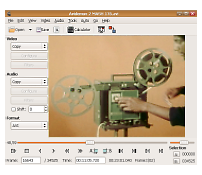 This is a nice, Open Source, package! If you want to “play” with video editing, this is a good way to get your foot “in the door” so to speak.
This is a nice, Open Source, package! If you want to “play” with video editing, this is a good way to get your foot “in the door” so to speak.