This article pitches the idea that passwords time has come. I have to admit, it would be nice to have a better token, but what would work well and still be secure?
Has the time come to kill the password?
Open Source – By: Scott Nesbitt – “How many passwords do you have? Probably more than you can easily remember or comfortably manage on your own. And I’m willing to bet that you dread coming up with new ones when you sign up for something online.
Jonathan LeBlanc of PayPal is on a mission is to replace the password with something more secure and easier to use.
He’s not a head-in-the-clouds dreamer or theorist, either. LeBlanc is head of developer advocacy for PayPal and Braintree, and has an abiding interest in security, identity, and social technologies. He’s also the author of Programming Social Applications and helped architect the developer authentication technology used by companies like PayPal and Yahoo.
At POSSCON 2015, LeBlanc will be giving a talked titled Kill All Passwords. I spoke to him to learn more about what’s wrong with the password and what can replace it.
What’s the problem with passwords?
The problem itself isn’t necessarily the password. The problem is that human beings are horrible at creating passwords that have any measure of complexity. If we look at the statistics on leaked passwords in 2014, approximately 5% of all people use password as a password. About 10% of the population uses either password, 123456, or 12345678. If we look at the top 1,000 leaked passwords, those account for 91% of leaked passwords.
We can build systems to perform device fingerprinting, location verification, and identification through usage habit identification, but all of that becomes secondary if password choices are weak.
How did we get to this point with passwords?
We’re human. We are inundated with technology and accounts day in and day out, and most people will choose a password that they can easily remember. That makes sense, but no matter how much we tell people that their password choices are incredibly insecure, people will still continue to use weak passwords and the same password on all of their accounts. We got to this point because we expected people to pick a convoluted series of multi-case characters, numbers, and symbols that means nothing to them in order to secure their accounts.
How did you get involved in this drive to kill the password?
This came naturally with the work that I have been involved in within the security and identity industry. About six years ago, when I was working at Yahoo, I was working with their OAuth 1 (later 1.0a) and OpenID integrations as well as some of the more experimental authentication technology that was used for their social logins and social application environment. This gave me my first real foray into some of the security architecture behind a login and has led to me helping to architect the authentication systems behind the PayPal developer products.
What I realized throughout all of this is that there is a fine line between the security of the systems and the usability of the systems. We had to find a balance where the user was protected as much as possible, but we were also able to give them an easy experience. This drive towards password-less authentication is an evolution of that.
Is there a way to make passwords secure that’s easy for everyone?
Absolutely. On the consumer side, password manager systems like 1Password or LastPass are becoming more prevalent and allow you to only remember one master password. Beyond that, your other accounts can have highly secure passwords that you have no way of remembering, and the system just remembers for you. Both personally and professionally, I use 1Password.
On the system side, we can further bring security to users by employing device and browser fingerprinting, region detection, and identification based on typical usage habits, all without the user having to be impacted the additional levels of security.
What can replace the password?
If we break down the concept of a username and password, they are an identification of who you are (the username) and then a verification of that fact with something that only you should know (the password). Any technology that provides these facilities can do that, so it’s not so much about keeping the username and changing the password, but really just about picturing these systems in a different way.
How will open source technologies play a role in replacing passwords?
On the data security side, to further secure username/password authentication, you have a number of open source key hashing and salting implementations. When used properly, they allow for the secure storage of user information, including those passwords.
Authentication and authorization technologies like OAuth 1.0a, OAuth 2, and OpenID Connect all provide a more secure implementation for logging a user in and allowing applications to do things on their behalf. They do more than secure information like passwords back and forth between an application and the login host.
As we start to explore biometrics, wearables, embeddable, and other technologies, they potentially become another factor in telling a system who you are. They can use multiple authentication factors to turn that into a valid login. Open source hardware, especially microcontrollers and sensors, is being used to build these next generation prototypes.
How secure are those technologies?
It really depends on what you’re trying to secure.
Let’s look at hashing for password security first. General purpose hash algorithms like MD5 and SHA1 are built for speed—to be able to handle as much data as possible in as short a time as possible. The problem with using those in password security is that since an attacker can’t reverse the hash, they might simply launch a brute force attack with different potential inputs until they generate the correct hash. The faster the hashing algorithm, the more viable this attack is.
Algorithms like bcrypt and PBKDF2 use a technique called key stretching. They allow you to determine how expensive (in terms of time and/or size) the hash function will be. We choose to make the decryption slower to prevent these potential attacks, but still make it fast enough to not impact a valid user. These algorithms are slow, but incredibly strong and secure.
With biometrics, one concern is something called a false positive rate. That’s how often an invalid user is seen as a valid user, and allowed access. Since most new studies on biometric authentication vary wildly, it’s difficult to determine exactly just how secure most of them are. Biometrics are a great mechanism for identifying you, but a second factor of authentication is needed. Of course, some biometrics sources are far superior than others when it comes to having low false positive rates. For instance, vein recognition technology, which measure vein uniqueness through blood flow, offers a higher level of security than fingerprint identification.
Which is the most promising of these technologies?
The work being done within the realm of biometrics through wearables, embeddables, injectables, and ingestibles, has a lot of promise. Realistically, it’s going to be the wearable devices and computers that maintain short term advances, as anything in the embeddable realm is not really seen as culturally acceptable by most of the population.
I think what we’re going to see are numerous mechanisms around personal identification, which uses a second factor of authentication that is accessible and known to the user, in order to target the username and password for potential dismissal. This realm, and the technology that powers it, is currently being explored in commerce, medical applications, and a number of other industries.
Where else are these technologies being used?
A lot of the work that is being done with the future of biometrics is coming from the commerce and medical industries.
Within PayPal, for instance, we’re working with partners who are building vein recognition technology, heart beat identification bands. We’re also part of the board of the FIDO Alliance, which seeks to create a unified specification for the future of identification. Within the medical industry, we’re seeing embeddable sensors and wearable computers as some of the first human-incorporated technology of a new potential future identity.
Are humans still the weakest link in the chain?
Yes, humans will always be the weakest link because the vast majority will always choose the path of least resistance over the one that provides them the most security. Really, though, technology implementations are just as much to blame in many cases. Secure methodologies, such as using a complex password that is not easy to guess, means that the person has to remember something that is meaningless to them, and it’s much harder to have our brains remember something that has no association to anything else.
Technology such as key managers, and others such as biometrics, are on the right path. The correct solution is to find the most secure way of providing authentication for the user without putting the onus on them for remembering the complexities of that authentication.
When do you see the password dying (if ever)?
The password won’t die, it will just change. Much of the identification technology that is being worked on in internet security, biometrics, or elsewhere, is looking at what a username and password actually are: identification of who you are and verification of that. Biometrics triggered through wearables, embeddables, or ingestible, second factor authentication systems, and many other technologies, are all rising to meet this challenge.”
 Turn your HD TV into a PC, OK, that would be cool!
Turn your HD TV into a PC, OK, that would be cool!


 We are closer to getting Amazon stuff via drone delivery!
We are closer to getting Amazon stuff via drone delivery!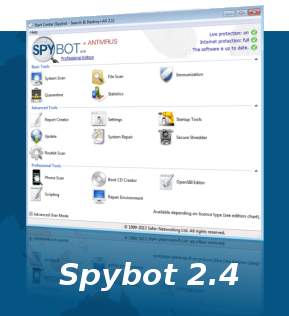 This is a first! I am posting an update of SpyBot, which I have mentioned before, because it is a very different, and improved product!
This is a first! I am posting an update of SpyBot, which I have mentioned before, because it is a very different, and improved product!